Software wiping vs physical destruction
The choice between software wiping and physical destruction isn’t a technical preference but rather a risk decision. The appropriate method depends on device condition, data sensitivity, reuse intentions, and the organisation’s risk tolerance.
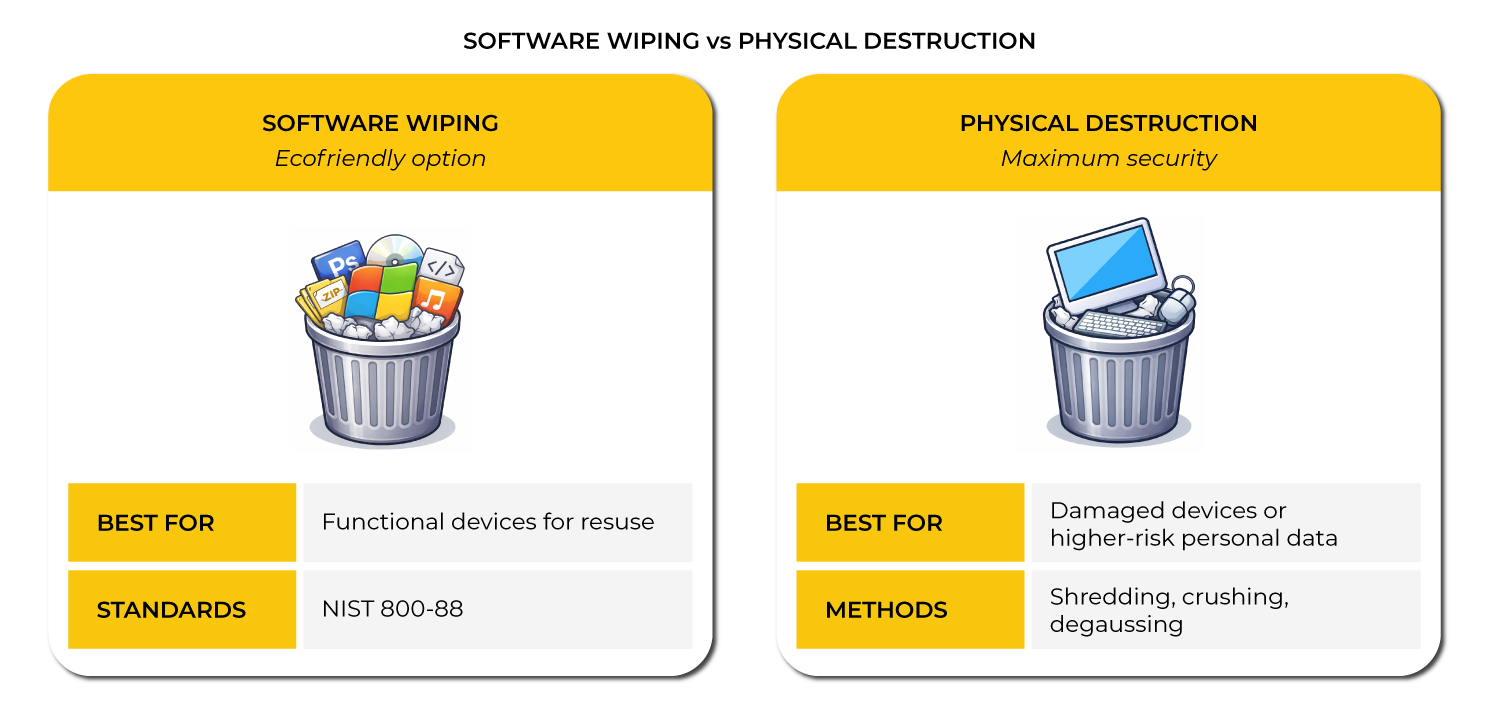
Software Wiping
This is best suited for functional devices intended for reuse or resale. Recognised standards include NIST 800-88 Rev. 2, which provides Clear, Purge, and Destroy guidance for different media types.
Software wiping supports environmental sustainability by enabling device reuse. However, some Hard Disk Drives (HDDs) and Solid State Drives (SSDs) may contain hidden blocks that sanitisation tools cannot overwrite, and non-functional drives cannot be reliably sanitised.
Physical Destruction
In all cases, destruction must be proportionate to risk. It’s typically appropriate when devices are damaged, at end-of-life, or contain higher-risk personal data such as special category dataTypes of personal data listed in Article 9(1) GDPR that are considered sensitive and thus require extra protection. Article 9(1) lists data relating to: • racial or ethnic origin • political opinions • religious or philosophical beliefs • trade union membership • genetic data • biometric data • health • sex life • sexual orientation Where these types of personal.... Common methods include shredding (often to 6-10mm particle sizes), crushing, and degaussing for magnetic media.
For larger organisations, physical destruction is generally delivered at scale through specialist providers. This approach supports consistency across sites, provides clear chain of custody, and standardised documentation.
Small companies may be able to carry out physical destruction internally, provided it is done using the right methods and controls. Where destruction is performed in-house, it’s essential to document when, how, and by whom, and to retain records confirming that data was rendered irrecoverable.